Sensor Based PUF IoT Authentication Model for a Smart Home with Private Blockchain | Semantic Scholar

Embedded Systems UDE on Twitter: "The Paper "Physical Unclonable Functions in the Internet of Things: State of the Art and Open Challenges" has been published in the journal "Sensors" . https://t.co/jMUDADFDYu #IoT #
presents a block diagram of the proposed PUF-based PKI protocol. If an... | Download Scientific Diagram
Dispositivos IoT con huella digital de silicio gracias a la función física no clonable aplicada en el proyecto Instet • CASADOMO
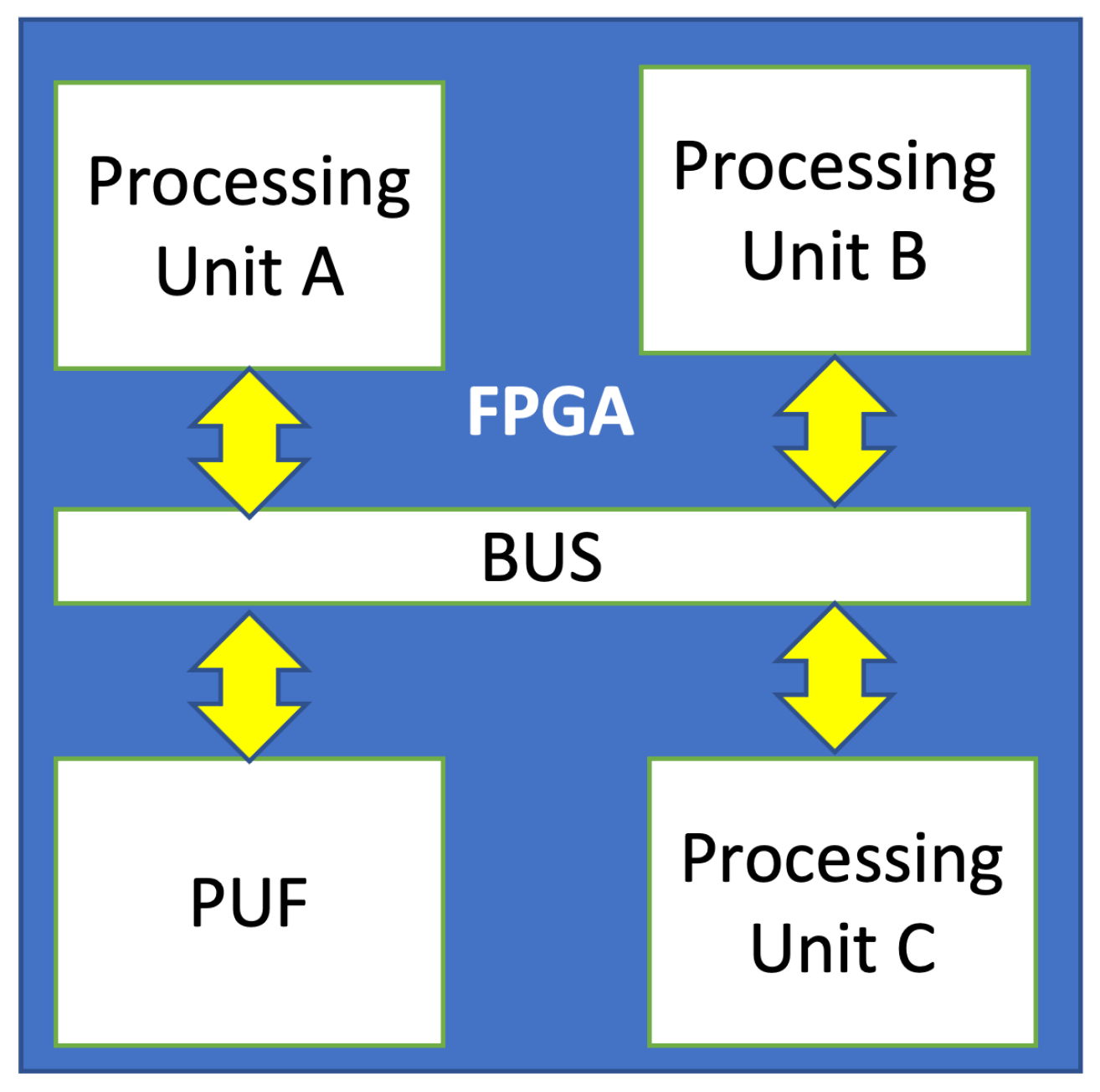
Sensors | Free Full-Text | Reconfigurable Security Architecture (RESA) Based on PUF for FPGA-Based IoT Devices | HTML

PDF) Implementation and Characterization of a Physical Unclonable Function for IoT: A Case Study With the TERO-PUF | Lilian Bossuet - Academia.edu